Networking
NuoDB processes communicate using TCP connections, running asynchronously whenever possible. For the system to work:
-
Each APs must be able to connect to all other APs
-
Each AP must be able to connect to the TEs and SMs that it is responsible for.
-
Within a given database, every TE and SM must be able to connect to every other TE and SM in that database.
-
TEs and SMs never connect to TEs or SMs in different databases.
-
These inter-process connections are often referred to as peering in our documentation.
Port Usage
NuoDB processes use the following ports.
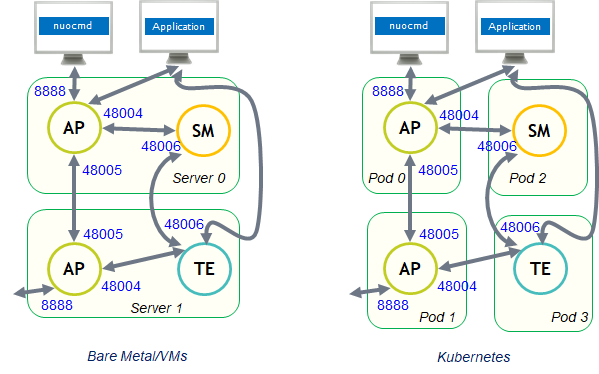
- Admin Processes
-
-
48004 - Clients, TEs and SMs use this port to talk to an AP.
-
48005 - This port is used by APs amongst themselves only.
-
8888 - The AP listens on this port for REST API connections, such as those from
nuocmdIt may use HTTP (default) or HTTPS (if TLS keys are defined).
-
- Engines
-
-
48006 - The default port for communications with an engine. The APs, TEs and SMs all use this port to talk to a given TE or SM.
-
48007 - If a second TE or SM runs on the same host, then 48007 is used (because 48006 is already taken).
-
48008+ - Ports above 48007 are used for each subsequent TE or SM on the same host.
-
Note that under Kubernetes, each AP, TE and SM runs in its own pod (a Linux namespace, a bit like a mini, virtual host), so ports 48007 and above are never needed.
Securing Communications
Out of the box, NuoDB expects TLS to be enabled to secure communications.
However, you are responsible for defining the necessary keys.
Once enabled, all internal communications are encrypted using the supplied keys.
The REST API is also encrypted and REST clients (including nuocmd) must use HTTPS.
If TLS is not enabled, communications within NuoDB are still secured using a form of Secure Remote Password (SRP).
SQL clients also switch to using SRP.
However, REST clients (including nuocmd) revert to HTTP, which is not encrypted.
Communication between database clients is always encrypted and the client can choose whether TLS or SRP is used.
For details see Enabling TLS in Bare Metal/VM Environments or Enabling TLS in Containerized Environments.